I have previously used Telerik Fiddler Everywhere to capture / analyse traffic between my iPad and Denon amplifier. It does an excellent job but is quite expensive to use regularly and a bit difficult to configure for occasional use. Wireshark is the best-known network analysis software and I wanted to familiarise myself further with its use.
Wireshark runs on Windows and can only analyse traffic through the ethernet or wifi interfaces, that is to say traffic to or from the PC. As a first example I decided to look at traffic to/from a Chrome session.
First Attempt : BBC
I picked www.bbc.co.uk as a frequently used web-site without advertisements.To identify BBC related packets in wireshark I need its ip address, which can be obtained using the nslookup command. Unfortunately the BBC web-site has a complicated front-end which is to be expected with a heavily used, high volume site and there are a number of possible IP addresses.
If I type www.bbc.co.uk into Chrome I am redirected to a signon screen.
Looking at wireshark I can see that a number of IP addresses are involved in the hand-shaking/retrieval of this first page.
Packet 3512 shows a request to www.bbc.co.uk port 80 (http) at 212.58.236.1
Packets 3513-3515 seem to show requests to port 443 (https).
Packets starting at time 19.769s (3507) through 19.86s (3544) appear to be part of this initial dialog.
It is much to complex for us to understand the way that the bbc is setup so I abandoned it.
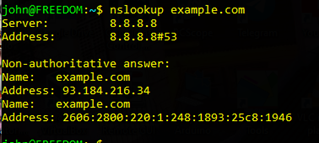
Second Attempt : example.com
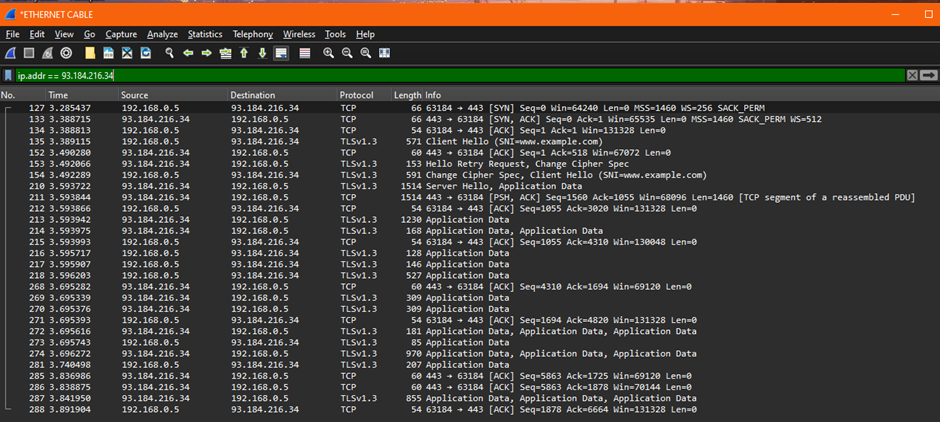
Typing in the URL https://example.com still gives us quite a lot of packets. Unfortunately the Protocol is TLSv1.3, so the packets are encrypted and it is not possible to work out what they contain.
As all internet pages need to use https, this approach isn't going to be very useful to me, but it is instructive to see some live internet traffic.
Third Attempt : local web page
I setup a simple web page test.html on my local raspberry pi web server so that I can get a more detailed view of traffic. I use wireshark to capture http packets from the web server
We can see the raw data on the right of the page and the formatted equivalent on the left.





No comments:
Post a Comment