In part one of this blog I refreshed my knowledge of wireshark by analysing traffic between a Windows PC browser session and a web-site. In practice my principal requirement is to analyse traffic from iPad apps to determine how they control the Denon amplifier and Pure Jongo funxtions.
Plan A : Wifi monitoring
The obvious way to capture packets is to use a "promiscous" wifi connection. By default ethernet adapters only pass relevant packets relevant to the attached computer. However if the ethernet adapter is in "promiscous" mode it can pass all packets for all devices on the ethernet LAN segment to the host. Unfortunately my ethernet card doesn't support promiscous (aka monitor) mode for wireshark packet capture.
Similarly it is sometimes possible to put a wifi adapter into monitor mode and capture packets relating to all devices using a network. Wireshark documentation makes it clear this isn't easy.
Following the wireshark instructions I check my Windows PC wifi adapter but it wasn't suitable for monitor mode. I then purchased a new wifi dongle which appeared to support monitor mode. Despite trying it on Windows and Linux there was no way I could get it into monitor mode. As I investigated a bit further the only instance I found of the card being used in monitor mode is with Kali Linux (used for network hacking and penetration testing), and it may have been necessary to have a special Kali configuration to achieve that.
On the basis that wifi monitoring is a specialised and difficult thing to do I decided not to investigate this avenue further.
Plan B : Proxy Server
Having given up on a wifi adapter the next idea was to direct traffic from the iPad via a proxy server on the PC to Denon / Pure devices. This is the approach used previously whereby I pointed the iPad at a Proxy Server running within
Fiddler Everywhere which then forwarded packets to Denon.
There are a
wide variety of Proxy Server configurations / uses. Often they are geared towards passing information from all local devices through to the internet. I wasn't able to find a suitable Windows proxy software program which looked likely to do what I wanted. If I want to progress this idea it would be better for me to use the solution which Fiddler Everywhere provides. A couple of weeks after my investigation I came across mitmproxy a HTTPS proxy application for Linux/Windows which may be a good solution.
Other approaches are available to route packets via the PC so that they can be captured. For example, tt is possible that a
wifi hotspot running on Windows will enable wifi packets to be captured. Again it is something I have not yet investigated.
Plan C : Mirror Port
One of the main issues with monitoring ethernet devices is that usually wireshark (and other software) can only capture packets which are addressed to the host PC. Network switches often have a feature called mirror ports which allow you to configure an ethernet port so that it receives a copy of traffic passing through another port on the same switch. I was pleasantly surprised to find that this feature is available on a cheap home hub so I purchased a suitable device.
My Denon amplifier has an ethernet socket as well as wifi so I connected my PC and amplifier to the hub, then configured the amplifier port so that it mirrored to the PC port.
The result is very impressive, I can now easily see all the commands used to control the Denon amplifier as they are sent from the Denon / Heos iPad apps and the responses sent back to the iPad.
For example, looking at the traffic captured above I see that the IPad is sending /
receiving HTTP/XML packets. Looking at packet 2415 from the iPad I see that it contains an XML command
requesting "current track position" info from Denon. I can send similar commands from a python script do do the same thing and thereby add current track position information to my web page used to control Denon.
Plan D : iPad Ethernet cable
Plan C was a great step forward, we have an easy way of capturing packets from any ethernet device which is close to the switch / PC.
I still have a problem with Pure Jongos. I use Jongos for multi-room audio. They allow you to stream audio to a number of devices and synchronise the sound so that you can move from room to room listening to music. As well as being a fraction of the cost of Sonos devices I can use Jongos to play music on my Denon amplifier and Yamaha soundbar in addition to Jongo smart speakers.
Although Jongos use the uPnp protocol I have not been able determine how to program them for multi-room audio. I am reliant on an iPad app to choose the music and synchronising playing - this is very irritating. As neither the iPad or Jongos have ethernet interfaces Plan C doesn't help me.
The solution turned out to be quite straighforward. I purchased a cheap iPad ethernet cable and plugged it in to a mirror port.
It is easy to enable the ethernet port and disable wifi. All packets to / from apps now pass through the ethernet mirrored port and can be captured by wireshark.
When I first tried to use the Pure, Denon and Heos apps they failed with error messages saying that wifi is required for using the app. This was worrying but I found that if I enabled wifi the traffic actually uses the ethernet port (as it is faster, "lower path cost" in routing terms) and I could see the necessary commands.
The packet shown above is actually the key to solving the problem which has been irritating me for the last few years. I knew that multi-room audio works with a bluetooth input. The packet above shows that I have to add Jongo devices to a Bluetooth group for multi-room to work. I can easily add this into a python script and control this from a web page.
I have been trying to get multi-room audio to work for about four years using Jongos. This is a quite a moment for me.
Plan E : Windows wifi hotspot
It is often the case that when writing up a topic you get a new idea which changes the whole picture. As I was writing this blog I thought that using the PC as a wifi hotspot seemed a bit similar to plan B, proxy server options so I decided to try it out. Fifteen minutes later I found that it works 😀. I can easily setup my PC wireless card as a
hotspot. When I do this, the PC has starts a network TotalFree and has an extra IP address 192.168.137.1 which will forward any packets it receives.
I configure my iPad to attach to TotalFree and it gets an IP address 192.168.137.37.
Now I can start wireshark using LAN connection *12 and it captures all traffic on TotalFree.
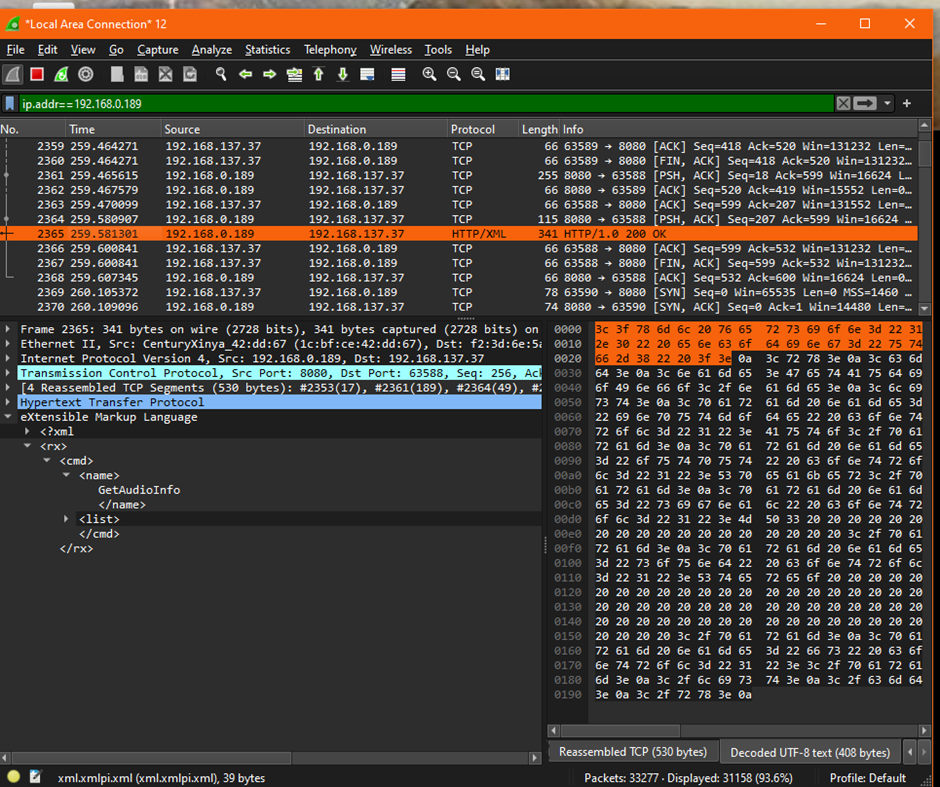
As a quick test I setup a display filter for the Denon Amp (on its usual wifi address 192.168.0.89) and I could look at HTTP/XML control packets as shown below.
This is an amazing simple solution which doesn't require any hub or ethernet cables and can be setup in a couple of minutes.
The solution doesn't actually work, as is, for Jongos since they need to be on the same wifi network. I would have to attach the Jongos to TotalFree.
Conclusion
These investigations have been a great help in allowing me to control my music devices from a python script / web page. In the past I have tried to solve technical problems using trial and error, being able to see communication in action makes it so much easier to understand what is happening.
The use of a mirror port and iPad ethernet cable remove much difficulty from monitoring a range of devices in wireshark. It is still necessary to understand which IP addresses to capture and the protocol in use but we are able to monitor a much wider variety of traffic than previously.